Every Thing You need to Know about Personally Identifiable Information (PII)
Marketing technology makes a lot of complex things possible in the present day and age. Marketing wasn’t as easy or effective back in time before the internet took over.
Marketers have a good understanding of how these systems work but all of that is surface-level knowledge. The real technological wizardry happens behind the curtains that enable functions like targeted ads, personalization, data analytics, attribution, etc.
But, how does all of this tracking happen? How does a system identify whether a user is an important decision-maker for some business or is a student trying to learn more about marketing?
The technology that is at the core of this identification functionality is known as personally identifiable information, often abbreviated as PII.
So, what is PII and what does it do? Let us answer that for you!
What Is Personal Identifiable Information?
There are several definitions of personally identifiable information, especially in the USA where there is no one legal term for it.
Going by the general consensus, personally identifiable information is any form of data that can be used by itself or in combination with other data to identify an individual.
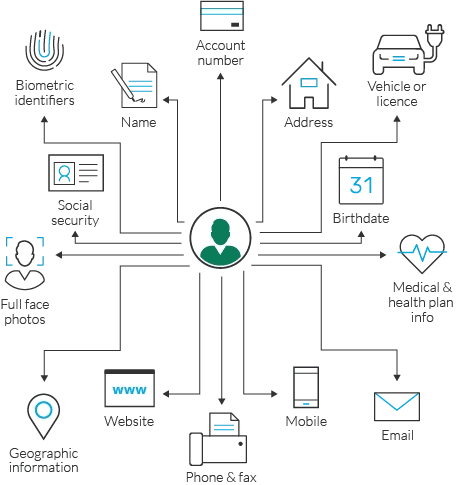
There are a lot of subsets in PII, there are direct identifiers such as passport number, social security number; quasi-identifiers such as name, race, date of birth.
Examples of non-sensitive identifiers are zip code, race, religion, place of birth, gender, etc. Identifiers such as full name, social security number, biometrics, medical records, etc. are sensitive identifiers.
Personally identifiable information has formed the bedrock of modern marketing as PII enables the majority of the marketing processes such as lead qualification, account-based marketing, personalization, and analytics to name a few.
But what types of data are considered PII data? We’ll list them down for you!
What Types of Data Qualify As PII Data?
For the sake of ease of understanding, we’ve listed down data types that qualify as PII data into two categories as below:
Sensitive Data
- Full name
- Home address
- Email address
- Social security number
- Passport number
- Driver’s license number
- Credit card numbers
- Date of birth
- Telephone number
- Owned properties e.g. vehicle identification number (VIN)
- Internet Protocol (IP) address
- Cookies
Non-Sensitive Data
- Country, State, Zip Code
- Race
- Gender
- Age
- Place of birth
- Religion
- Level of Education
The main reason for categorizing PII data into these two categories was to address the growing concerns about online privacy. Knowing what data a site tries to collect from you can help you safeguard your online privacy.
On that note, many people often end up confused and use the terms personal data and personally identifiable data interchangeably. While the naming of these terms is enough to warrant the confusion, let us learn what makes these two different.
Personal Data vs PII
Let’s start with knowing what Personal Data is!
The European Union’s General Data Protection Regulation, commonly abbreviated as GDPR is considered the foundation on which the data protection and privacy regulations have been standardized across the internet.
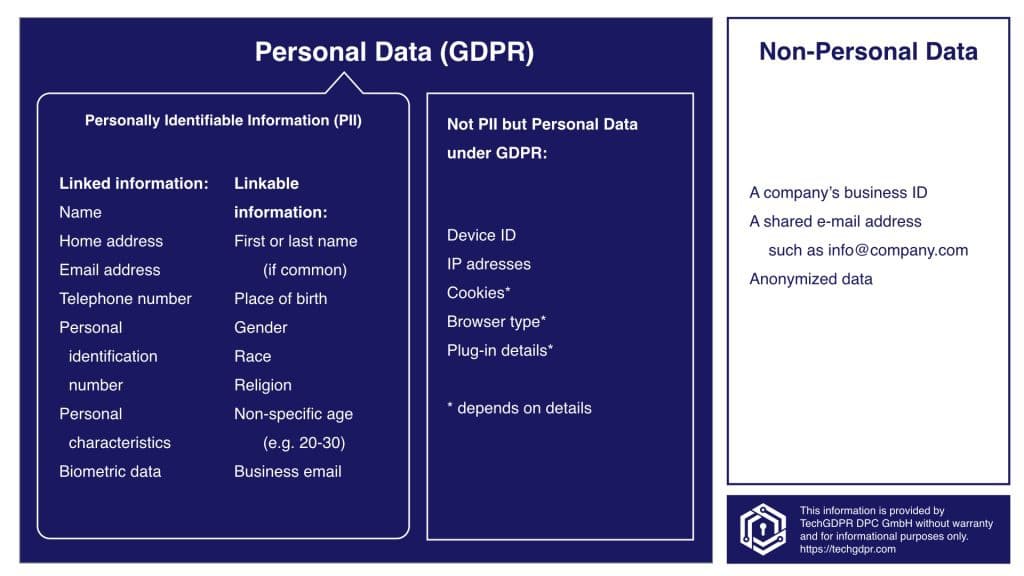
According to GDPR, any form of data relating to an identified or identifiable natural person (data subject) is personal data. An identifiable person is one who can be identified, directly or indirectly, using these forms of identifier data.
Examples of these identifiers are name, identification number, location data, an online identifier, or one or more factors specific to the physical, physiological, genetic, mental, economic, cultural, or social identity of that natural person.
We’ve seen what personally identifiable information means and constitutes. Based on that knowledge we can discern that PII is a subset of Personal Data.
So personal data encompasses personally identifiable data and other forms of data too.
The types of data under PII are specifically used to identify or distinguish an individual from other users on the internet while personal data types store personal information of all sorts.
This means all and any form of PII is subject to data protection and privacy laws and regulations that govern the handling, use, storage, and security of personal data by various entities on the internet.
We hope you’ve gained clarity about these two terms. Continuing on, we shall see how sensitive and non-sensitive data differ from one another.
Sensitive Data vs Non-Sensitive Data
While data privacy laws and regulations have mandated all websites and online platforms to acquire user permission for collecting and storing user data, it is necessary to know which data types you should allow to be collected and stored.
We have listed down the data types previously in this blog, here we will provide a clear distinction between the two data types.
Sensitive Data
The information collected under this data type is generally not available in the public domain and usually is provided by the user to the entity requesting the data.
While information such as contact number, email id, address, credit card number, etc. are commonly required to avail various services provided online, these pieces of information in the wrong hands can cause a lot of trouble for the user.
Not only do such pieces of information reveal your identity but they also provide misusers of such information with a way to reach you for various ill intents and purposes.
Identity theft is yet another major issue that may arise out of your sensitive information leaking onto the internet and then landing in the wrong hands.
Non-Sensitive Data
The information classified under this data type is generally available in the public domain and can be accessed for various purposes. Such pieces of information aren’t exact and do not allow for direct identification of an individual.
Age group, gender, educational level, area of residence, religion, race, etc. are the types of data that are considered under this category. These allow for the profiling of an individual on the internet but mask the individual’s identity.
This level of information is enough to provide a certain degree of personalization and other features too.
So now you know what types of information you need to be careful about before providing them to websites or online platforms.
But how is the data that you provided used and safeguarded against any misuse?
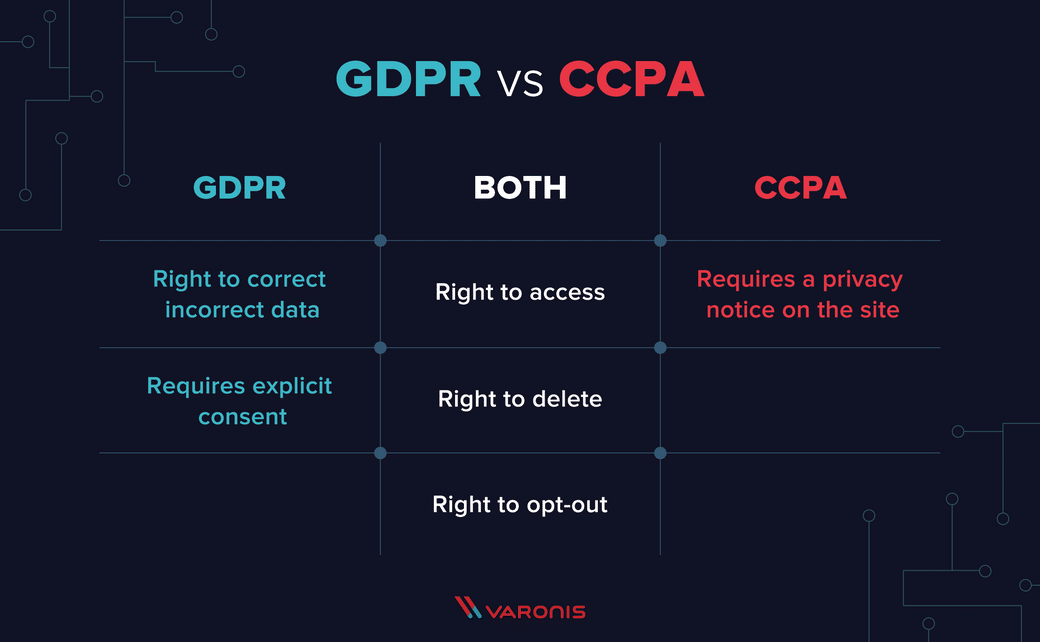
Usage and Protection of PII Data Under GDPR
Though GDPR was adopted and implemented in Europe, the framework of data safeguards and usage policies have found worldwide adoption.
The following points will provide you with more insights about it all:
- GDPR applies to all businesses within the EU and even those outside the EU servicing and catering to the EU citizens.
- Every online entity must disclose what information they need from the user.
- They must also inform the user as to how the information will be used and strictly adhere to that declaration.
- Every online entity is required to acquire consent from the users to collect and store the information.
- They are also required to disclose how long the information will be stored.
- The users can deny permission to collect and store data about them and all online entities have to conform to their decision.
- In case of a data breach resulting in a leak of personal information of the users, the affected online entity has to inform GDPR within 72 hours of the event occurring.
- Citizens have a lawful right to ask for their information to be securely deleted. Their information cannot be shared or used for any other purposes without acquiring consent for the same.
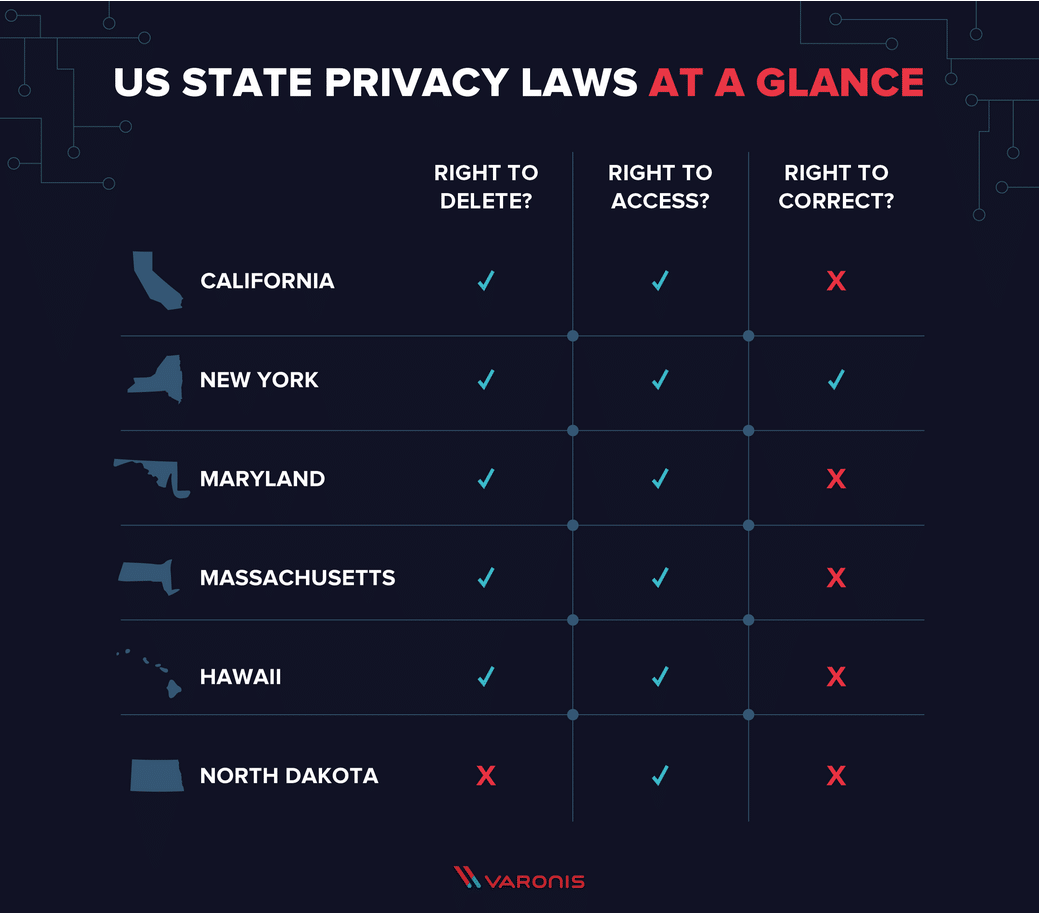
Usage and Protection of PII Data in Non-EU Countries
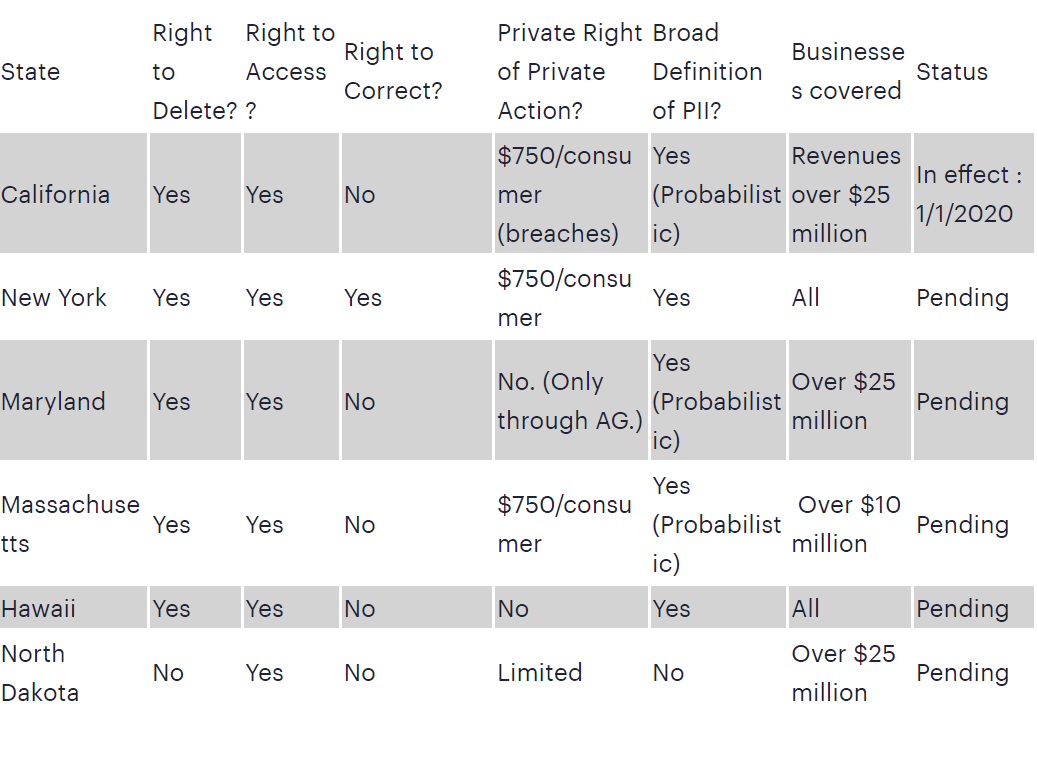
- The US has no federal-level laws and regulations dictating the usage and protection of PII data. However, various states have come up with their own laws that regulate the storage and usage of PII data.
- California is leading the charge for data privacy advocacy with its California Consumer Privacy Act (CCPA). Considering the concentration of the tech industry inside California, it is safe to say that the majority of the US internet users’ data is safe.
- With data privacy movements gaining pace, other states have also come up with bills to regulate the use and storage of PII data. Most states are framing their laws by studying how GDPR works and building upon it.
Many US states have a data privacy and regulation law in the pipelines, with several states even entitling users with compensation for their data leaking via a data breach. Though late, the US’s online landscape will soon be a safer place.
- While the laws are yet to be implemented in many states, a lot of tech giants have already started to incorporate changes that are in line with their GDPR compliant regulations in the EU region.
- In May of 2017, Japan formulated and implemented the Personal Information Protection Act (PIPA), the act dictated how the data needs to be collected, used, and stored with consent and how it is to be transferred or shared with third parties and internationally.
- The Bureau of Indian Standard has the data privacy and usage framework under the works under the IS 17428. The upcoming law will mandate acquiring consent, de-authentication, encryption, local storage of data, and other measures to safeguard user data.
Conclusion
The best way to keep your identity and data safe in the online world is to be educated about how things are, how they work, and how to minimize risks. If you are a business, it is equally your responsibility to protect customer data and educate them about data you are tracking.
We hope this blog has helped you with all those points!
Recently, it was found that users can be identified using their graphic card’s performance signature. The only way to avoid such risks is to stay updated with all developments from time to time.
So be aware and protect customer data!
Sell more, understand your customers’ journey for free!
Sales and Marketing teams spend millions of dollars to bring visitors to your website. But do you track your customer’s journey? Do you know who buys and why?
Around 8% of your website traffic will sign up on your lead forms. What happens to the other 92% of your traffic? Can you identify your visiting accounts? Can you engage and retarget your qualified visitors even if they are not identified?